Security By Design: minimize your attack surface
Security by design is a 360° software development technique that emphasizes on security throughout the development process, instead of treating it as an afterthought. This principle implies the implementation of security at all levels of the software development life cycle (SDLC), including during requirements gathering, design and implementation.
« Security by Design is a holistic approach to software development that emphasizes on security throughout the process. »
Security by design is all about minimizing the potential attack surface, which implies that developers should assume that users will make mistakes and include adequate protection methods in their code.
Integrating security into applications can be difficult because some attacks are difficult for humans to anticipate.
One way to improve the odds of avoiding these vulnerabilities is to consider how attackers might try to break into the system and then implement countermeasures accordingly.
A software secure by design
As part of the development of secure by design digital services, developers have the daunting task of securing their applications. They must protect against malicious attacks while providing the necessary application functionality.
The difference compared to traditional systems is the anticipation of the threat upstream rather than the reaction afterwards. All in all, this helps to design a safer and more resilient IT architecture.
The difficulty with the “security by design” approach lies mainly in the developers' ability to retain control of the system as a whole. It is therefore essential to make the right choices at the start by limiting the potential attack surface, and therefore to limit the number of uncontrolled third-party components.
Dependency Management and Audit
A software dependency is often the tree that hides the forest, importing a single library can lead to a cascade of potential flaws: one library depends on another, which depends on another,...
Guaranteeing and maintaining the reliability of a system will strongly depend on the elements that compose it, which is why an in-depth audit is necessary to qualify the attack surface exposed by third-party components. And this, throughout the life cycle of the application.
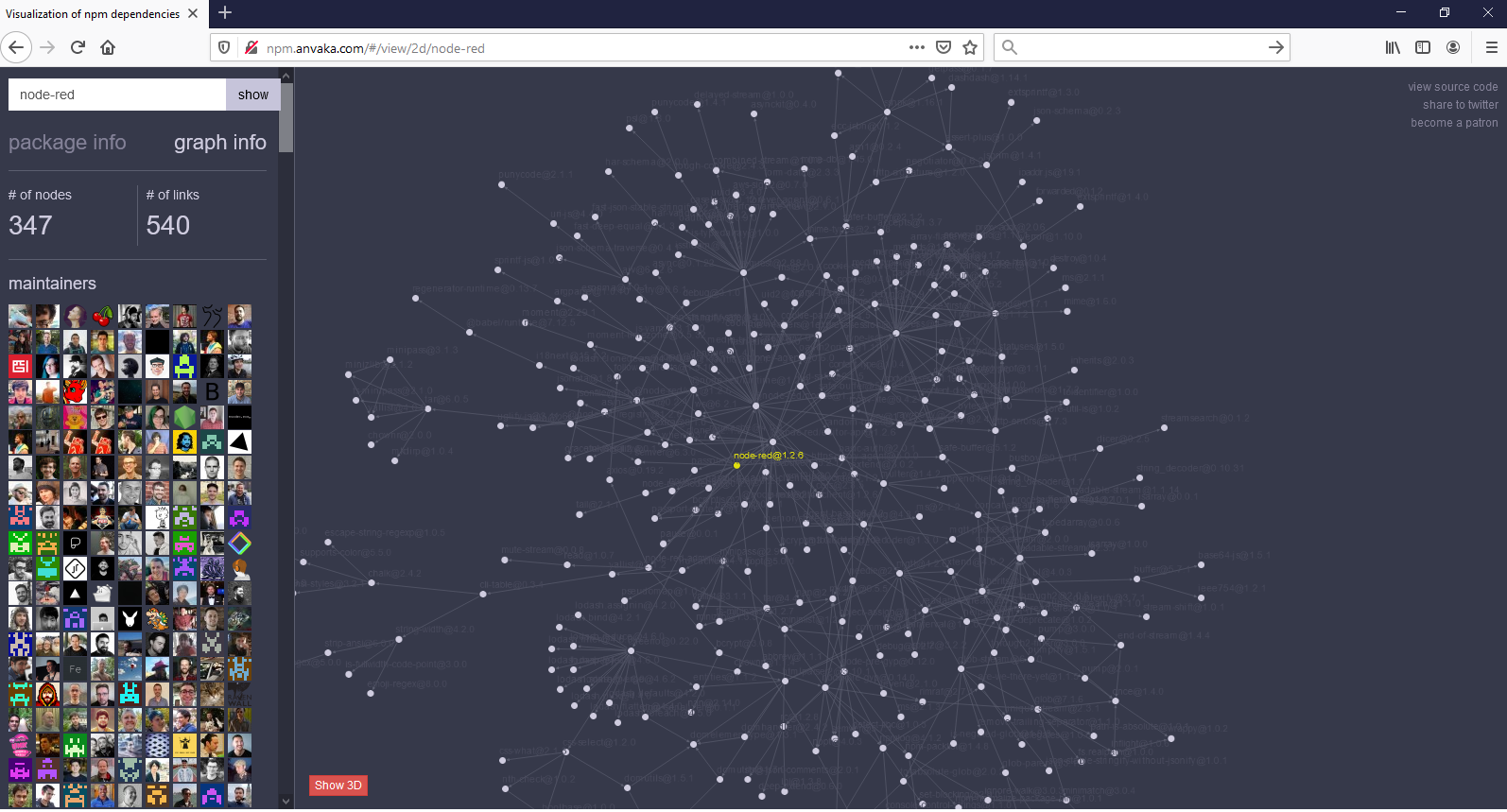
Limit the attack surface
The Aeonics solution is in itself secure by design, the number of dependencies is nil which greatly limits the attack surface.
Developer-designed microservices automatically benefit from a proven security context. The functionalities deployed in serverless mode with Aeonics therefore benefit de-facto from a secure by design approach.
Aeonics as a tool simplifies the development of secure by design applications, while keeping developers in control of their code.



